DataStax Enterprise
How to configure DataStax Enterpise
Requirements:
- Configure Windows Server (How to configure Windows Server 2008 for DSE)
- Configure Linux (How to configure Linux for DSE)
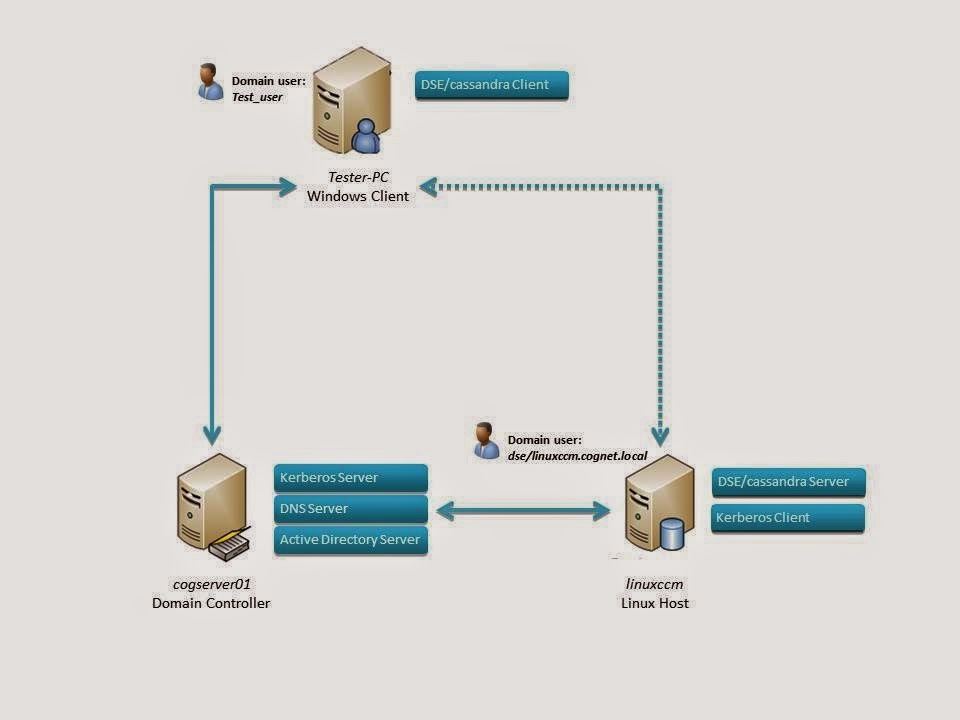 |
| Scheme DSE network |
1. Kerberos configuration Windows Server
1.1 Active Directory Users and Computers > Users > test_user (cassandra user) and dse/linuxccm.cognet.local (cassandra server) > properties > tab account > Account options > set options:
·
Use
Kerberos DES encryption
·
The
account supports Kerberos AES 128 and 256 bit encryption
(see images below)
 |
Account
options for “test_user” user (cassandra client)
|
 |
| Account options for "dse/linuxccm.cognet.local" user (cassandra server) |
1.2 Add group (Account Operators) for test_user (cassandra client) and dse/linuxccm.cognet.local (cassandra server) > properties > tab Member Of
Run ADSI Edit > Action > Connect > CN=cognet > CN=Computers > CN="Tester-PC"(cassandra client) > Properties > Tab Attribute Editor > msDS-SupportedEncryptionTypes > set value: for users 0x1B, for computers 0x1F. (see images below)
1.4 And attribute: UserAccountControl > Add bit 0x200000 for enable DES key only

More information: Ktpass settings
If ok (see image below),
4. Add Cassandra user:
create user for example:
4.5 Check /etc/hosts (see image below)
The package installation process will step through defining the basic Kerberos configuration parameters. Recommended settings are:
Create the Kerberos database with the following command:
Add a user:
8. Testing kerberos configuration
Run DSE/Cassandra
To test the operation of Kerberos, request a Ticket-Granting Ticket (TGT) with the kinit command
Use the klist command to verify the TGT is valid:
9. DSE
line 86 comment out:
line 88 uncomment:
10. Testing DSE with Kerberos authentication
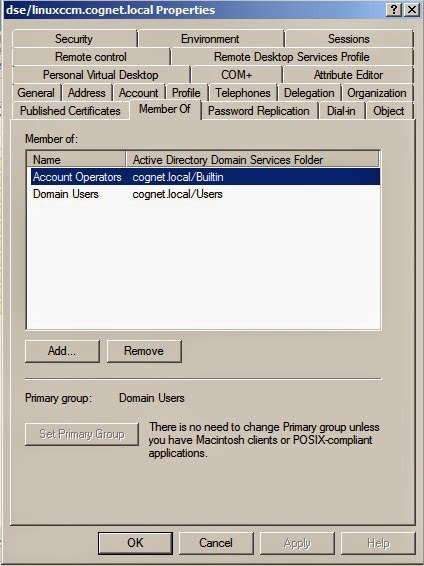 |
| Add
group for "dse/linuxccm.cognet.local" user (cassandra server) |
 |
Add group for "test_user" user (cassandra client) |
1.3 For dse/linuxccm.cognet.local (cassandra server) > properties > tab Delegation > set Trust this user for any services ( Kerberos only)
 |
| Set trust for "dse/linuxccm.cognet.local" user (cassandra server) |
Run ADSI Edit > Action > Connect > CN=cognet > CN=Computers > CN="Tester-PC"(cassandra client) > Properties > Tab Attribute Editor > msDS-SupportedEncryptionTypes > set value: for users 0x1B, for computers 0x1F. (see images below)
 |
| Supported
encryption for "TESTER-PC" computer (windows client) |
 |
Supported
encryption for "test_user"
user (cassandra client)
|
1.4 And attribute: UserAccountControl > Add bit 0x200000 for enable DES key only
For computers 0x81000, for users linux 0x290200, for users windows 0x210200.
 |
| Attribute:
UserAccountControl for "test_user" user (cassandra client) |
 |
| Attribute:
UserAccountControl for "dse/linuxccm.cognet.local" user (cassandra server) |
 |
Attribute:
UserAccountControl
for
"Tester-PC" computer (windows
client) |
1.5 Enable the following Group Policies to apply the DES encryption type to all computers that are running Windows 7(Tester-PC) or Windows Server 2008 R2 (cogserver01):
- Run gpedit.msc (win button > type gpedit.msc) > Computer Configuration > Windows Settings > Security Settings > local policies > Security options > Network security: Configure encryption types allowed for Kerberos >Tab: Local security settings set as image below (set local security options) enable all encryption type.
1.6 Create account mappings
a. Start the Active Directory Users and Computers snap-in. Point to Programs, then Administrative tools, and then Active Directory Users and Computers.
b. Start advanced features by clicking View, and then Advanced Features.
c. Locate the account where you want to create mappings, and right-click on user to view Name Mappings. This example uses the account test_user.
d. Click the Kerberos Names mappings tab.
e. Add a principal from the foreign MIT (based on UNIX) realm. The example shown in Figure 10 below users test_user@COGNET.LOCAL (this user must create in Cassandra and Kerberos database)
For dse/linuxccm.cognet.local add kerberos principal: dse/linuxccm.cognet.local@COGNET.LOCAL (this user must create in Cassandra and Kerberos database)

1.7 Create keytab (on Domain Controller) for Linux
Run cmd > type:
C:> Ktpass -princ dse/linuxccm.cognet.local@COGNET.LOCAL -mapuser linuxccm -pass Cognitum2014 -crypto DES-CBC-MD5 -ptype KRB5_NT_PRINCIPAL -out c:/dse.keytab
More information: Ktpass settings
2. Configuration Kerberos on Linux
2.1 DSE installation
2.1.1 Register and download DSE (tarball version ) on Linux:
$ java –version
Use the latest version of Oracle Java 6 or 7 on all nodes. If you need help installing Java, see Installing the Oracle JRE and JNA.
Check which installed Java you use and choose recommended version Java:
$ sudo update-alternatives --config java
2.1.3 Unpack the distributions:
$ tar -xzvf dse.tar.gz
2.1.4 Delete gz file:
$ rm *.tar.gz
More information about installation tarball version: install tarball
2.2 Copy keytab from Domain Controller (C:/dse.keytab) to Linux (<dse_dir>/resources/dse/conf)
2.2.1 Edit cassandra.yaml file (<install_location>/ resources/ cassandra/ conf).
line 266,357,391
2.2.2 Edit cassandra-env.sh file (<install_location>/resources/cassandra/conf/cassandra-env.sh.)
comment out:
JVM_OPTS="$JVM_OPTS -Denable-old-dse-state=true"
and:
JVM_OPTS="$JVM_OPTS -Dcom.sun.management.jmxremote.port=$JMX_PORT"
If use Java 7 or later comment out:
if [ "$JVM_VERSION" \> "1.7" ] ; then
JVM_OPTS="$JVM_OPTS -XX:+UseCondCardMark"
Fi
Use the latest version of Oracle Java 6 or 7 on all nodes. If you need help installing Java, see Installing the Oracle JRE and JNA.
Check which installed Java you use and choose recommended version Java:
2.1.3 Unpack the distributions:
2.1.4 Delete gz file:
2.2 Copy keytab from Domain Controller (C:/dse.keytab) to Linux (<dse_dir>/resources/dse/conf)
2.2.2 Edit cassandra-env.sh file (<install_location>/resources/cassandra/conf/cassandra-env.sh.)
comment out:
JVM_OPTS="$JVM_OPTS -XX:+UseCondCardMark"
Fi
3. Check the DSE
3.1 Run DSE (with parameter cassandra) for example:
$. /<install_location>/bin/dse cassandra
3.2 Run putty on another computer (for example Client PC) and connect with Ubuntu
type:
$./<install_location>/bin/cqlsh <ip_Linux>
3.3 Download driver
3.4 Copy drivers to client computer (on Windows Client)
Cluster cluster = Cluster.Builder().AddContactPoint("192.168.0.116")
in Project Playground in Program class, change ip (192.168.0.116) to ip Linux[linuxccm]
type:
$./<install_location>/bin/cqlsh <ip_Linux>
3.6 First open “release_1_0_0_dse” driver (<csharp-driver_dse>\Cassandra.MyTest.sln)
3.7 Edit line
Cluster cluster = Cluster.Builder().AddContactPoint("192.168.0.116")
in Project Playground in Program class, change ip (192.168.0.116) to ip Linux[linuxccm]
If ok (see image below),
Then edit cassandra.yaml file (<install_location>/resources/cassandra/conf).
line 85 comment out:
authenticator: org.apache.cassandra.auth.AllowAllAuthenticator
line 86 uncomment:
#authenticator: org.apache.cassandra.auth.PasswordAuthenticator
line 100 comment out:
authorizer: org.apache.cassandra.auth.AllowAllAuthorizer
line 101 uncomment:
#authorizer: org.apache.cassandra.auth.CassandraAuthorizer
4. Add Cassandra user:
Restart DSE:
$sudo killall java
$./<install_location>/bin/cqlsh <ip_Ubuntu> -u cassandra -p cassandra
$./<install_location>/bin/cqlsh <ip_Ubuntu> -u cassandra -p cassandra
create user for example:
CREATE USER test WITH PASSWORD 'foo' SUPERUSER;
CREATE USER 'test_user@COGNET.LOCAL' WITH PASSWORD 'Cognitum2014' SUPERUSER;
CREATE USER 'dse/linuxccm.cognet.local@COGNET.LOCAL' WITH PASSWORD 'Cognitum2014' SUPERUSER;
CREATE USER 'test_user@COGNET.LOCAL' WITH PASSWORD 'Cognitum2014' SUPERUSER;
CREATE USER 'dse/linuxccm.cognet.local@COGNET.LOCAL' WITH PASSWORD 'Cognitum2014' SUPERUSER;
4.1 Start the Visual Studio 2010(on Windows Client) snap-in or later version visual studio.
4.2 Open “release_1_0_0_dse” driver (<csharp-driver_dse>\Cassandra.MyTest.sln)
4.3 Edit Playground/Program.cs line 44 from
4.4 Run Playground (If you see the message in the image below, then the DSE with password authentication runs ok)
or run debug-cql(on Linux Host):
· Run debug-cql that interaction would look like:
user@LinuxCCM:~/DSE/dse-3.2.4/resources/cassandra/bin$ ./debug-cql 192.168.1.1 9042
CQL binary protocol console 192.168.1.1@9042
Connecting...
>> STARTUP
-> AUTHENTICATE org.apache.cassandra.auth.PasswordAuthenticator
>> AUTHENTICATE username=test password=foo
-> org.apache.cassandra.transport.messages.AuthSuccess@3e0ebb
CQL binary protocol console 192.168.1.1@9042
Connecting...
>> STARTUP
-> AUTHENTICATE org.apache.cassandra.auth.PasswordAuthenticator
>> AUTHENTICATE username=test password=foo
-> org.apache.cassandra.transport.messages.AuthSuccess@3e0ebb
5. KDC Setup
$ sudo apt-get install krb5-kdc krb5-admin-server
$ sudo dpkg-reconfigure krb5-kdc
$ sudo dpkg-reconfigure krb5-kdc
The package installation process will step through defining the basic Kerberos configuration parameters. Recommended settings are:
· disable Kerberos 4 compatibility mode
· do not run krb524d (daemon to convert Kerberos tickets between versions)
· defaults for the other settings are acceptable
Here is an example configuration file(/etc/krb5kdc/kdc.conf):
Supported_enctypes we are using only des-cbc-md5:normal
Edit file /etc/krb5kdc/kadm5.acl:
$sudo krb5_newrealm
6. Realm Administration: kadmin
To start the kadmin utility, issue the following command:
$sudo kadmin.local
Add a user:
kadmin: addprinc test_user
Add a service:
kadmin: addprinc dse/linuxccm.cognet.local
7. Client configuration
Edit /etc/krb5.conf (as in the image below)
8. Testing kerberos configuration
Run DSE/Cassandra
$<install_location>sudo bin/dse Cassandra
To test the operation of Kerberos, request a Ticket-Granting Ticket (TGT) with the kinit command
$ kinit –p test_user@COGNET.LOCAL
Password for test_user@COGNET.LOCAL:
Password for test_user@COGNET.LOCAL:
Use the klist command to verify the TGT is valid:
$ klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: test_user@COGNET.LOCAL
Valid starting Expires Service principal
02/11/14 08:07:14 02/11/14 18:09:43 krbtgt/COGNET.LOCAL@COGNET.LOCAL
renew until 02/12/14 08:07:14
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: test_user@COGNET.LOCAL
Valid starting Expires Service principal
02/11/14 08:07:14 02/11/14 18:09:43 krbtgt/COGNET.LOCAL@COGNET.LOCAL
renew until 02/12/14 08:07:14
9. DSE
9.1 Edit dse.yaml (<install_location>/resources/dse/conf) (as in the example below).
keytab: resources/dse/conf/dse.keytab
service_principal: dse/_HOST@COGNET.LOCAL
http_principal: HTTP/_HOST@COGNET.LOCAL
qop: auth
service_principal: dse/_HOST@COGNET.LOCAL
http_principal: HTTP/_HOST@COGNET.LOCAL
qop: auth
9.2 Edit cassandra.yaml file (<install_location>/resources/cassandra/conf).
line 86 comment out:
authenticator: org.apache.cassandra.auth.PasswordAuthenticator
line 88 uncomment:
#authenticator: com.datastax.bdp.cassandra.auth.KerberosAuthenticator
9.3 Edit Playground/Program.cs line 44 from .WithAuthProvider(new PlainTextAuthProvider("test","foo")) to
10. Testing DSE with Kerberos authentication
10.1 To work around debug-cql, you can just disable JMX option in cassandra-env ((<install_location>/resources/cassandra/conf/Cassandra-env.sh) by commenting out this line:
JVM_OPTS="$JVM_OPTS -Dcom.sun.management.jmxremote.port=$JMX_PORT"
(found 13 lines from the bottom of the file)
10.2 Run DSE/Cassandra
$<install_location>sudo bin/dse Cassandra
If you want more information about debugging run dse with parametr JVM_OPTS="-Dsun.security.krb5.debug=true"(debugging info) and –f (foreground):
$<install_location>sudo JVM_OPTS="-Dsun.security.krb5.debug=true" bin/dse cassandra –f
10.3 Run debug-cql
a) Set ticket for user:
$ kinit –p test_user@COGNET.LOCAL
b) Check generated ticked:
$ klist
c) Run debug-cql that interaction would look like:
$<install_location>/resources/cassandra/bin$ JVM_OPTS="-Dkerberos.enabled=true" ./debug-cql linuxccm.cognet.local 9042 CQL binary protocol console linuxccm.cognet.local@9042
Connecting...
>> STARTUP
-> AUTHENTICATE com.datastax.bdp.cassandra.auth.KerberosAuthenticator
>> AUTHENTICATE
-> org.apache.cassandra.transport.messages.AuthSuccess@1b0bdc8
Connecting...
>> STARTUP
-> AUTHENTICATE com.datastax.bdp.cassandra.auth.KerberosAuthenticator
>> AUTHENTICATE
-> org.apache.cassandra.transport.messages.AuthSuccess@1b0bdc8
If you want more information about debugging run debuq-cql with parametr JVM_OPTS="-Dsun.security.krb5.debug=true”(debugging info):
$<install_location>/resources/cassandra$ JVM_OPTS="-Dsun.security.krb5.debug=true -Dkerberos.enabled=true" bin/debug-cql linuxccm.cognet.local 9042
11. Troubleshooting
Kerberos is fairly fault-tolerant, if the requisite services are in place. If Kerberos authentication fails, check the following:
A. The user has a valid ticket (use klist).
B. “Authentication requires both 'username' and 'password'” check file cassandra.conf
C. “Unable to obtain Princpal Name for authentication” check files: dse.keytab, /etc/krb5.conf, /etc/krb5kdc/kdc.conf and list_principals($sudo kadmin.local, then list_principals) if principal doesn’t exists, create account ($sudo kadmin.local,then add_princ name), principal must have the same account in cassnadra database and AD users.
D. “Unable to obtain password from user”
a) Check the contents of the keytab with: klist -e -t -k /path/to/keytab
b) Use the
kinit utility to verify that Kerberos is set up properly and that your principal and keytab are valid: kinit -k -t keytab-file account-name
c) Check supported encryption in settings on domain controller(ADSI edi, gpedit.msc and Active Directory Users and Computers)
d) Restart all machine (important is restart Domain controller(cogserver01))
e) Then generate again keytab:
Ktpass -princ dse/linuxccm.cognet.local@COGNET.LOCAL -mapuser linuxccm -pass Cognitum2014 -crypto DES-CBC-MD5 -ptype KRB5_NT_PRINCIPAL -out c:/dse.keytab
f) Copy keytab to Linux host
g) Edit dse.yaml file (authentication doesn't run correctly change keytab path to direct path).
E. “kinit: KDC has no support for encryption type while getting initial credentials”
kinit fails with complaint about encryption type
To fix, edit /etc/krb5.conf file, and in the [libdefaults] section add
To fix, edit /etc/krb5.conf file, and in the [libdefaults] section add
allow_weak_crypto = true
or reset password for test_user
The clocks of the KDC and local machine aren’t synchronized. Check date and format of date.
$date
Wed Nov 2 15:52:07 MYT 2011
$ ntpdate -u 192.168.1.200
2 Nov 15:39:37 ntpdate[7948]: step time server 192.168.1.200 offset -751.194050 sec
Wed Nov 2 15:52:07 MYT 2011
$ ntpdate -u 192.168.1.200
2 Nov 15:39:37 ntpdate[7948]: step time server 192.168.1.200 offset -751.194050 sec
G. Basic network connectivity is available (use ping and nslookup).
H. Forward DNS hostname lookup succeeds on both the KDC and the local machine.
I. Reverse DNS lookup succeeds on both the KDC and local machine, or dns is set to false in krb5.conf
J. The clocks of the KDC and local machine are synchronized.
K. The file permissions for various critical files such as /etc/krb5.keytab are correct and accessible by the user or service in question.sudo -u <username> can be helpful for this.
Following the KDC logs while attempting an operation can also be very informative. The following lines in /etc/krb5kdc/kdc.conf will enable KDC logging:
[logging]
kdc = FILE:/var/log/krb5kdc.log
kdc = FILE:/var/log/krb5kdc.log
If you had to edit kdc.conf to enable logging, restart the KDC to apply the changes:
$ sudo service krb5-kdc restart
Once logging is enabled, you can follow the log while attempting an operation:
$ sudo tail -f /var/log/krb5kdc.log

Cognitum provides IT solutions in the area of Cloud, BigData and Semantic Technology for customers both in Poland and abroad.












“I’m looking for a qualified professional to write my essays.” Say no more. We are the best option to write your essays. Here’s why. First, we care about every customer https://rankmywriter.com/essaypro-com-review of ours, and hence we always aim to improve their experience with us thanks to our well-trained client support.
ReplyDeleteIn view of the multiple benefits of the cloud, operators are adopting the technology throughout their network and IT applications in order to give countrywide coverage. In order to provide its retail and business customers a greater experience, Vodafone Idea is rolling out a cutting-edge, autonomous multi-cloud network across the nation. For its network and IT applications, it is also introducing a sizable integrated cloud platform, and it has worked with Cisco to build a distributed multi-cloud architecture. Applications, operating systems, infrastructure, and the underlying IP/MPLS (internet protocol/multiprotocol label switching) core are coordinated using this automated cloud scale architecture. You can download here >> for more info.
ReplyDeleteAdam,
https://www.youtube.com/watch?v=VuRAEaaSOaM
ReplyDeleteWhen I'm doing my homework, it's a huge help. It provides the most recent and best tips and techniques for creating books in simple language so that anyone can read them. That is why I believe the routine report writing service is a very useful educational service.
For example, assume a person is 카지노사이트 making $5 bets on each spin of the roulette wheel, and the wheel spins 50 instances an hour. While the person betting additionally be} successful some bets and shedding different bets, they're wagering $250 an hour. If the home edge performs out completely, on the end of 4 hours of play, they lose $50, or 5% of $1,000—an quantity 10 instances larger than they had anticipated. So while craps moves at a hundred or so rolls per hour and blackjack about 60 hands per hour, roulette moves at a more stately tempo -- roughly forty five spins per hour.
ReplyDeleteTruck accidents demand skilled legal representation. Our team of seasoned attorneys specializes in advocating for victims of truck collisions. With years of experience, we navigate the complexities of trucking regulations and insurance claims to ensure our clients receive fair compensation for their injuries, medical bills, and lost wages. From negotiating with insurance companies to litigating in court, we tirelessly pursue justice for those affected by negligent truck drivers or companies. Trust our expertise to guide you through the legal process and fight for your rights.
ReplyDeletetruck accidents lawyers
Configure each node in the DataStax Enterprise cluster. This includes setting parameters such Geometry Dash as heap size, disk storage options, network settings, and JVM settings. Ensure that each node meets the hardware and software requirements specified by DataStax.
ReplyDeleteEntering the world of That's Not My Neighbor , you will be transported into an experience full of drama and mystery. In a peaceful neighborhood, there's a mysterious neighbor, someone who doesn't belong here, and your mission is to find them before they disappear. With competition and tension increasing, you will have to combine observation, intelligence and communication to solve the mystery. But be careful, because not everyone is a cooperative person. In "That's Not My Neighbor", the struggle between trust and doubt will lead you to unexpected surprises, and only the one who grasps the mystery will have a chance to win. Are you ready to face the challenge and uncover the mystery of this strange neighbor?
ReplyDeleteComprehending the intricate legal terrain around traffic infractions in Loudoun County necessitates proficiency and intelligence. A skilled lawyer is essential whether you're dealing with DUI charges, reckless driving charges, or speeding fines. A knowledgeable attorney can make all the difference in defending your rights and minimizing the repercussions in Loudoun County, where traffic regulations are strictly enforced.loudoun county traffic attorney
ReplyDeleteConfiguring DataStax Enterprise (DSE) involves several steps, especially for integrating with Kerberos authentication on both Windows Server and Linux environments. Incredibox
ReplyDeleteConfiguring DataStax Enterprise (DSE) Bou's Revenge involves several steps, from installation to configuration for optimal performance and integration with other tools.
ReplyDeleteThe Geometry Dash endless supply of custom levels, coupled with engaging music and addictive gameplay, ensures players keep coming back for more.
ReplyDeleteDSE is designed to handle large volumes of data across distributed systems while maintaining continuous uptime and fault tolerance, making it perfect for mission-critical applications. DataStax Enterprise is a powerful solution for organizations wishing to build data-driven applications at scale while keeping flexibility and durability. It includes built-in security, automated administration tools, and enterprise-grade support. solicitation of prostitution defense
ReplyDeleteConfiguring DataStax Enterprise (DSE) Sprunki involves several key steps to ensure that the environment is set up correctly for optimal performance.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteKenyan content creators use Tubidy Mp3 to download viral trends, popular challenges, and social media videos, keeping up with the latest viral moments and creating engaging content, all while working in areas with unreliable internet service.
ReplyDeleteDSE is ideal for mission-critical applications because it can manage massive data volumes across dispersed systems while preserving fault tolerance and continuous uptime. For businesses looking to develop data-driven applications at scale while maintaining flexibility and durability, DataStax Enterprise offers a potent solution. It has enterprise-grade support, automated administration tools, and built-in security. Filing Bankruptcy in Virginia
ReplyDeleteMelon Playground is not just a game—it’s a playground for your imagination. So many tools, so much freedom!
ReplyDeleteCompetitive players will Speed Stars Online enjoy refining their starts, mid-race tempo, and finish bursts as they perfect every split-second decision in pursuit of the perfect sprint.
ReplyDeletecapybara clicker dynamic environment, made possible by its excellent sound design, is sure to inspire.
ReplyDeleteWant a game that’s easy to pick up but hard to stop playing? Stickman Hook is your next mobile obsession.
ReplyDeleteWhether you're deploying DSE for the first time or optimizing an existing environment, this blog provides a valuable resource to help you configure the platform effectively and leverage its full potential for scalable, real-time data management.
ReplyDeletefirst time disorderly conduct charge
Observe obstacle patterns in tap road to improve your reaction timing.
ReplyDeleteTech blog cognitum is a technology-focused blog that shares insights, updates, and analyses on the latest IT trends and innovations. It covers topics such as software development, cybersecurity, cloud computing, and emerging technologies. The blog provides practical tips, tutorials, and expert opinions for tech enthusiasts and professionals. Readers can stay informed about industry developments and best practices. Overall, it serves as a resourceful platform for learning, problem-solving, and staying updated in the tech world.
ReplyDeleteSEO Company In Delhi NCR
SEO Company in Delhi
Setting up DataStax Enterprise (DSE) can seem daunting at first, but with the right guidance, it becomes a streamlined process. This blog walks you through the essential steps to get your DSE environment up and running smoothly.
ReplyDeletedui lawyer hampton va
Configuring DataStax Enterprise involves installing the software, setting up cluster topology, and configuring nodes through cassandra.yaml and DSE-specific settings. Adjust replication, security, workload types, and performance parameters. Enable analytics, search, or graph features as needed. After configuration, validate cluster health using nodetool and monitoring tools for optimal operation. fast affordable virginia divorce lawyers
ReplyDeleteThe blog serves as a knowledge hub for professionals, students, and tech enthusiasts. Its content simplifies complex technologies, making them easy to understand and apply. The goal is to keep readers informed about the latest trends and advancements in technology.
ReplyDeleteBLVK
R789 Game is an online gaming platform that offers players a mix of entertainment and the chance to earn real money. It features a variety of games, including popular card games, slots, crash games, and other skill‑ and chance‑based options that appeal to different types of players.
ReplyDeleteThe blog serves as a knowledge hub for professionals, students, and tech enthusiasts. Its content simplifies complex technologies, making them easy to understand and apply. The goal is to keep readers informed about the latest trends and advancements in technology.
ReplyDeleteTadhana Slots 777
This blog provides accurate and helpful guidance. It’s written in a way anyone can understand. habeas corups lawyer california
ReplyDeleteThis blog post provides a clear and informative overview of DataStax Enterprise, effectively highlighting its strengths in scalability, security, and performance. The explanation of how it addresses big data challenges is concise and well-structured, making it accessible even to readers new to NoSQL platforms. To improve engagement, you could add a brief real-world use case or industry example. Similar clarity and reliability are valued in academic support, which is why Rapid Assignment Help focuses on structured solutions. Students searching for Do My Assignment For Me UK services can relate to the need for dependable, high-performance support.
ReplyDeleteThis is a comprehensive guide to configuring DataStax Enterprise, especially covering the intricacies of Kerberos authentication. It's great to see such detailed steps for both Windows and Linux environments. For anyone looking to get quick summaries of technical videos to support their learning, checking out the YouTube Transcript Generator can be a real time-saver.
ReplyDeleteThis is a very detailed guide on configuring DataStax Enterprise, especially the Kerberos authentication which can be quite complex. Image to Pixel Art, AI Cleaner Text
ReplyDeleteAI Cartoon Generator
Attractiveness Test
AI Image Generator By Nano Banana Pro
Converter PNG to SVG
MD to Word Converter
Merge JPG